Every Windows user installs an Antivirus to safeguard their computers. Still, it is not enough to protect your computer, and you should take more precautions to defend your computers from online malware threats. You can make your PC security more robust by blocking EXE files from vulnerable folders such as Temp, AppData, etc.
Also Read: How to add a folder to Microsoft Defender Controlled folder access in Windows 11?
Despite all proper countermeasures, there’s still a chance of getting infected. For example, if malware manages to enter your system by exploiting one of the various temporary folders that are provided by your OS to install new applications, unzipping compressed archives, storing temp data, etc.
“C:\Windows\Temp” works like a launchpad for viruses and malware. Apart from that, other risky folders are the following:-
- %USERPROFILE%\AppData\Local\ and all its subfolders.
- %USERPROFILE%\AppData\Roaming\ and all its subfolders.
Since all these folders are meant for storage and not for executables to run, finding a way to prevent potentially harmful .exe files from running from them would be an excellent extra layer of defense.
In this gearupwindows article, we will guide you through the steps on how to block .exe files from running on a Windows client or Windows Server by applying Software Restriction Policies.
How to Block EXE Files in Vulnerable Folders from Running in Windows 11 or 10?
To block running EXE files from vulnerable folders on Windows 11 or 10, use the following steps:-
Step 1. First, open Local Group Policy Editor (Windows 11/10 Home editors will need to enable gpedit.msc on their computers).
Step 2. When the Local Group Policy Editor window appears on your PC, browse to the following path in the left side pane:-
Computer Configuration > Windows Settings > Security Settings > Software Restriction Policies
Step 3. Right-click on the Software Restriction Policies folder and select New Software Restriction Policies in the context menu.
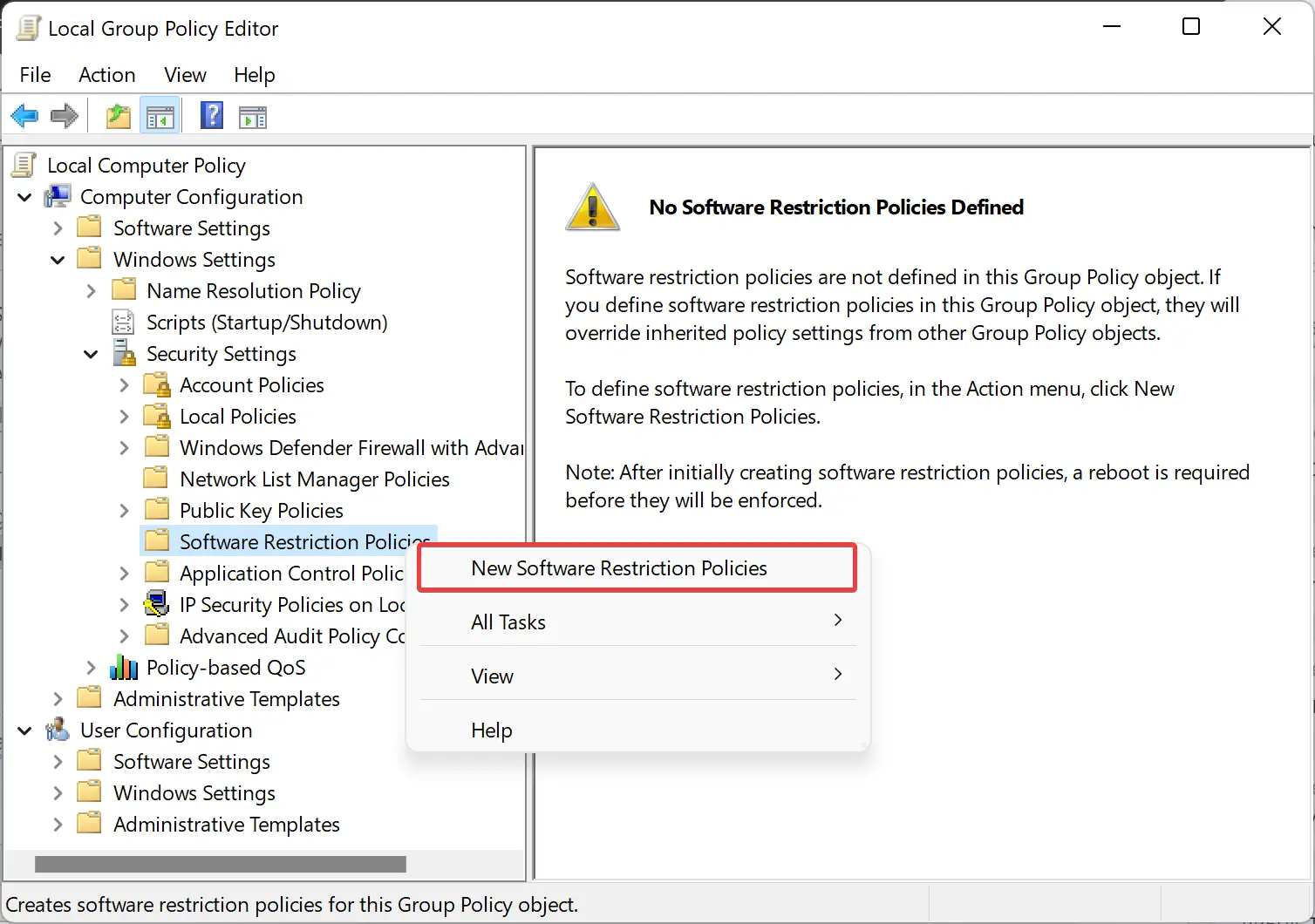
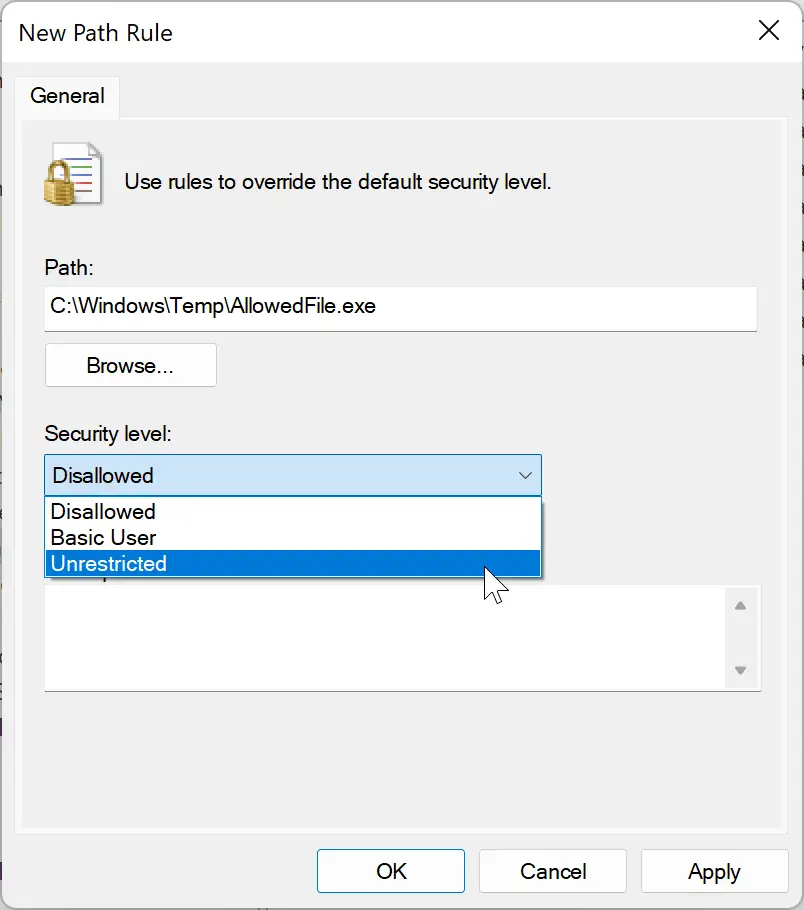
Step 4. When you’re done, Windows will create some new subfolders. Right-click on the Additional Rules and choose New Path Rule.
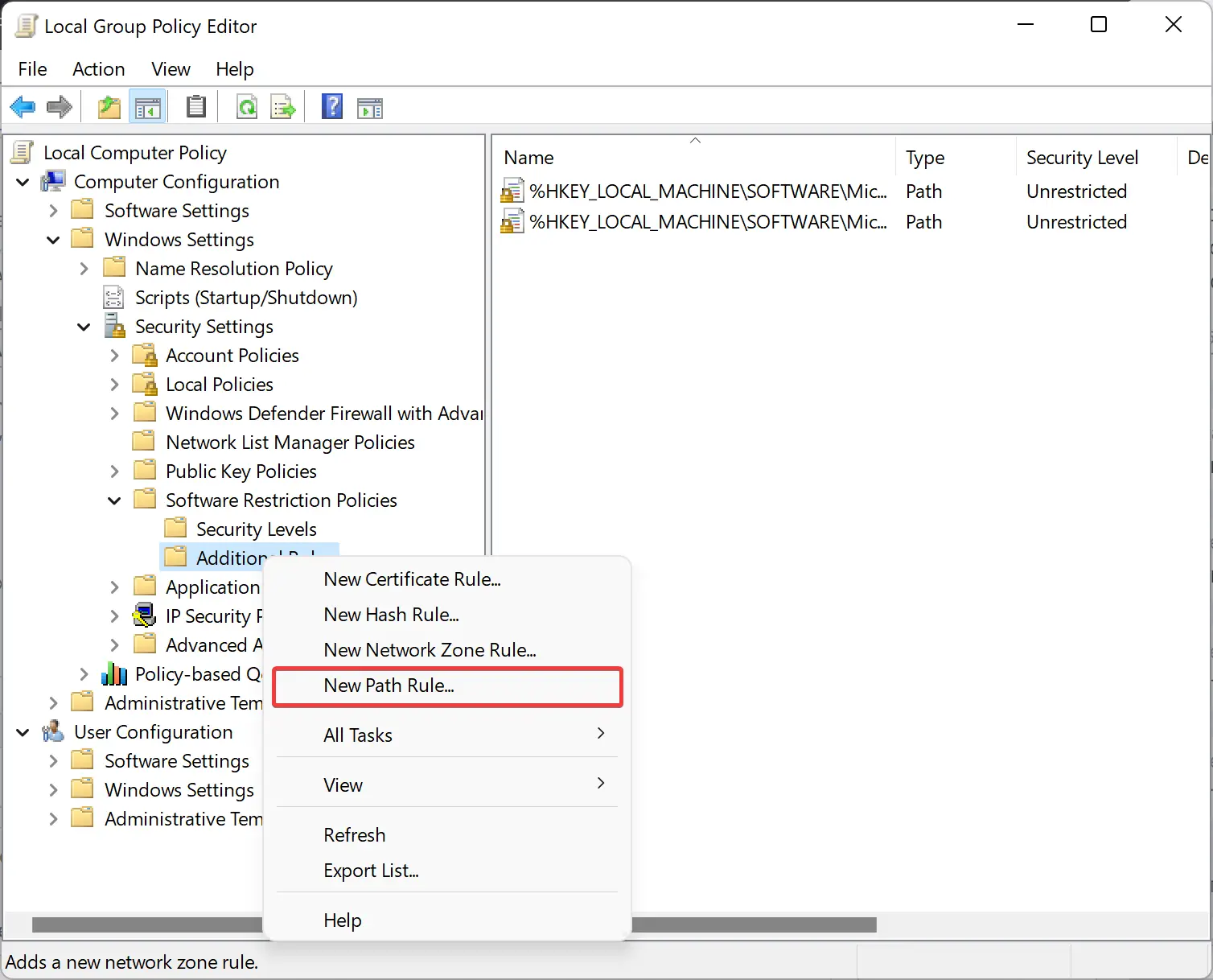
Step 5. In the “New Path Rule” window that appears, enter the path of the executable file that you want to stop from running. Ensure to put the *.exe at the end to block only executable files.
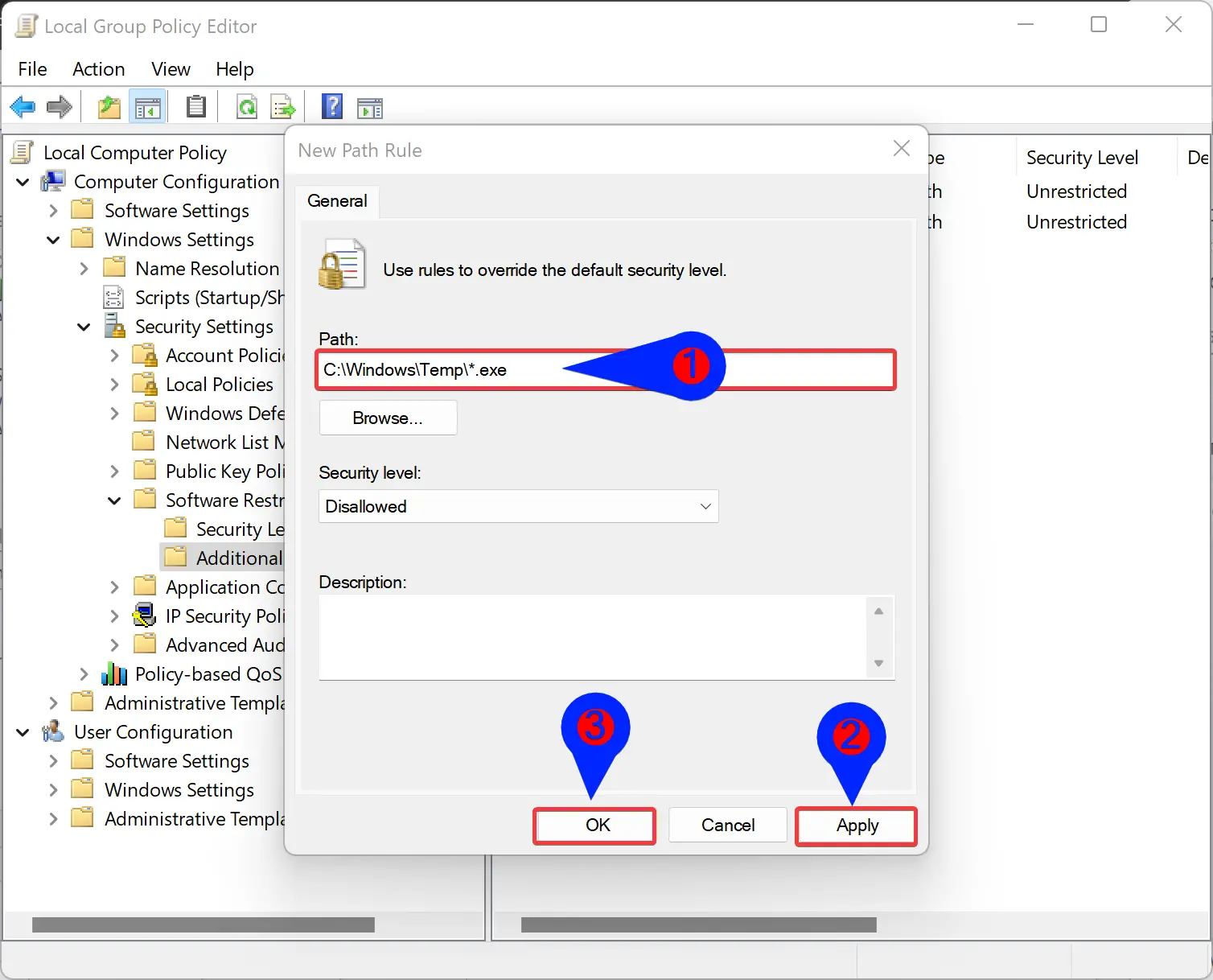
Step 6. Click Apply.
Step 7. Click OK.
We suggest you to block the following:-
- C:\Windows\Temp\*.exe
- C:\Windows\Temp\*\*.exe
- %USERPROFILE%\AppData\Local\*.exe
- %USERPROFILE%\AppData\Local\*\*.exe
- %USERPROFILE%\AppData\Roaming\*.exe
- %USERPROFILE%\AppData\Roaming\*\*.exe
Once done, this will block most potentially unsafe executables from running on your computer, including those coming from archive attachments opened using the Windows built-in zip support.
For some reason, if you want to allow a .exe file from the blocked folder, create a “New Path Rule” by selecting the Unrestricted option in the drop-down menu “Security level.”
Conclusion
In conclusion, it is essential to take all possible precautions to protect your computer from malware and other online threats. While installing an antivirus is a good start, it is not enough to safeguard your computer completely. In addition to using antivirus software, blocking EXE files from vulnerable folders such as Temp, AppData, etc., can make your PC security more robust.
This article has provided a step-by-step guide on how to block EXE files from running in Windows 11 or 10, using Software Restriction Policies. By following the suggested paths to block, users can prevent the most potentially harmful .exe files from running on their computers. This extra layer of defense can help protect users from malware that might have managed to enter their system by exploiting one of the various temporary folders provided by their OS.
While there’s still a chance of getting infected despite all countermeasures, taking these steps can significantly reduce the risk of malware infections. By staying vigilant and adopting these protective measures, users can keep their computers safe and secure from online threats.